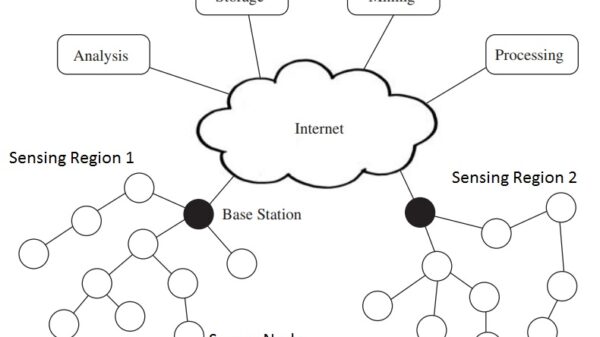
Cyber intelligence is the process of collecting, analyzing, and disseminating information about threats to an organization’s computer systems and networks. It is used to help organizations understand the threats they face, identify vulnerabilities, and develop mitigation strategies.
Cyber intelligence can be gathered from a variety of sources, including:
- Publicly available information: This includes news articles, social media posts, and other sources that are available to the public.
- Dark web intelligence: This includes information that is shared on the dark web, a part of the internet that is not indexed by search engines and requires special software to access.
- Human intelligence: This includes information that is gathered from human sources, such as informants or employees of targeted organizations.
Once information is gathered, it is analyzed to identify trends, patterns, and potential threats. This information is then disseminated to decision-makers within the organization so that they can take steps to mitigate the risks.
Cyber intelligence can be used to help organizations in a variety of ways, including:
- Preventing attacks: By understanding the threats they face, organizations can take steps to prevent attacks from happening. For example, they can patch known vulnerabilities, implement security controls, and train employees on security best practices.
- Responding to attacks: If an attack does occur, cyber intelligence can help organizations to respond quickly and effectively. For example, they can use the information to identify the attackers, track their movements, and disrupt their activities.
- Investigating incidents: Cyber intelligence can be used to investigate security incidents, such as data breaches and malware infections. By understanding the incident, organizations can learn from their mistakes and take steps to prevent similar incidents from happening in the future.
Cyber intelligence is a critical tool for organizations of all sizes. By gathering, analyzing, and disseminating information about threats, organizations can improve their security posture and protect themselves from cyber attacks.
The Cyber Threat Intelligence Lifecycle
The cyber threat intelligence lifecycle is a process that organizations use to collect, analyze, and disseminate cyber threat intelligence. The lifecycle typically includes the following steps:
- Collection: The first step is to collect information about cyber threats. This information can be gathered from a variety of sources, such as publicly available information, dark web intelligence, and human intelligence.
- Analysis: Once information has been collected, it must be analyzed to identify trends, patterns, and potential threats. This analysis can be performed by a team of analysts or by using automated tools.
- Dissemination: The final step is to disseminate the cyber threat intelligence to decision-makers within the organization. This can be done through a variety of channels, such as reports, briefings, and alerts.
The cyber threat intelligence lifecycle is an ongoing process that should be continuously updated as new information becomes available. By following the lifecycle, organizations can improve their ability to understand and respond to cyber threats.
Benefits of Cyber Intelligence
There are many benefits to using cyber intelligence, including:
- Improved security posture: By understanding the threats they face, organizations can take steps to improve their security posture and protect themselves from cyber attacks.
- Reduced risk of data breaches: Cyber intelligence can help organizations to identify and mitigate vulnerabilities that could be exploited by attackers. This can help to reduce the risk of data breaches.
- Improved incident response: If an attack does occur, cyber intelligence can help organizations to respond quickly and effectively. This can help to minimize the damage caused by the attack.
- Increased compliance: Cyber intelligence can help organizations to comply with regulations, such as the General Data Protection Regulation (GDPR).
Challenges of Cyber Intelligence
There are also some challenges associated with using cyber intelligence, including:
- Data quality: The quality of cyber intelligence can vary greatly. It is important to carefully evaluate the source of the information and the methods used to collect it.
- Interpretation: Cyber intelligence can be complex and difficult to interpret. It is important to have a team of experienced analysts who can understand the implications of the information.
- Sharing: Cyber intelligence can be sensitive and confidential. It is important to have a process in place for sharing the information with the right people.
Conclusion
Cyber intelligence is a valuable tool that can help organizations to improve their security posture and protect themselves from cyber attacks. However, it is important to be aware of the challenges associated with using cyber intelligence and to take steps to mitigate them.thumb_upthumb_downuploadGoogle itmore_vert